Insight
Making business sense of cyber risk
Ask any C-suite executive what’s keeping them awake at night and cyber attacks will be high up the list.
With the cyber security threat landscape continually shifting and attacks becoming more sophisticated, it’s becoming harder to identify the most pressing risks and take decisive action to mitigate them.
How can business leaders with no deep technical knowledge protect their organisations when hard-pressed cyber teams can find it difficult to communicate the risks in an intelligible, digestible and actionable way? How can executive teams judge where resources can be most effectively targeted and align cyber security with business strategy and risk tolerances?
Click on the links below to discover the key cyber-related questions (and their answers) for leadership teams to consider, no matter their role:
Get on top of your cyber risks
Discover the key cyber-related questions and their answers for each member of your leadership team to consider.
CEO
Strengthen your security and readiness to respond. Read more.
CIO
Allocate the right roles and responsibilities. Read more.
CHRO
Create a culture of security across your organisation. Read more.
NED
Know the right questions to ask to cut through the jargon. Read more.
CFO
Ensure external stakeholders are satisfied. Read more.
Head of Procurement
Ensuring your supply chain security. Read more.
CISO
Improve your ability to navigate the cyber landscape. Read more.
CRO
Enhance your security and risk management. Read more.
In line with current trends, the cost of cyber attacks to businesses worldwide is expected to rise to more than $20 trillion by 2027. It’s not just individual companies that are at risk of being hacked or held to ransom. Recent events show how whole economies can be paralysed in a matter of hours.
Why are cyber security threats escalating? Part of the answer lies in the combination of digital proliferation and today’s ever more extended digital ecosystems, much of which are spread across multiple third-parties. Businesses are only as secure as the weakest links in their value chain.
The other big factor in raising threat levels is geopolitical conflict. State-sponsored perpetrators and criminal gangs are using techniques developed in cyber warfare to disrupt businesses and critical infrastructure. They’re also adding tech-enabled advances such as generative artificial intelligence (GenAI) and deepfake manipulation to their already formidable armoury.
Increasing demand for cyber security from regulators
Regulation is also ramping up, from the EU Networks and Information Systems Directive (NIS-2) to mandatory incident reporting under new US Securities and Exchange Commission (SEC) cybersecurity rules. Sector-specific demands include the incoming EU Digital Operational Resilience Act (DORA) for financial services businesses.
Common themes cutting across this latest regulatory push include safeguarding critical infrastructure and boosting transparency over attacks and their impact. This not only raises the bar for protection and incident readiness, but also executive-level accountability, especially now there are provisions in the UK and US to hold company directors individually liable for major cyber security failures.
Insurers are increasing the focus by demanding more information about the maturity of safeguards and resilience before agreeing to underwrite cyber risks.
When we’re called in as cyber security consultants
With the threats rising, as cyber security consultants, we’re helping our clients proactively strengthen their cyber capabilities and operational resilience. Our support extends from helping clients to set their security strategy and deliver on the resulting roadmaps to increase their security posture, through to ensuring they are managing their cyber risk effectively with their executive teams and Boards. We also receive requests for assistance after an attack – helping our clients to perform cyber security reviews and deliver remediation programmes to make things right after the fact.
Cyber projects can be daunting as a result of their technical complexity and broad user impact. A good example is Identity and Access Management (IDAM) projects. But you can cut through the complexity and simplify the process. We’ve helped several clients such as Primark, IAG and Brambles deliver these complex security projects by taking project leadership roles.
Increasingly, we’re also being called in to provide FCA Section 166 skilled persons reviews on cyber defences. This reflects regulators’ growing spotlight on cyber (operational) resilience and need for additional assurance that risks are being appropriately managed.
Struggling to cut through the changing cyber threat landscape
Are businesses keeping pace with these fast-shifting threats? In many cases, no. Frequently, Chief Information Security Officers (CISOs) and their cyber security teams find themselves battling to cope with under-resourcing and mounting shortages of cyber specialists. For CISOs and their teams, the difficulties are compounded by the challenges of assessing, articulating and communicating today’s cyber risks in a way that executive teams and Boards can genuinely understand. This can create multiple challenges with cyber risk management and reporting. For example, some reports are crammed with technical jargon and lacking in business context, while others are too generic to provide real insight for executive leadership. Similarly, some risk evaluations are based on poorly evidenced quantification or a tendency to measure too much, while others are overly reliant on emotion and intuition.
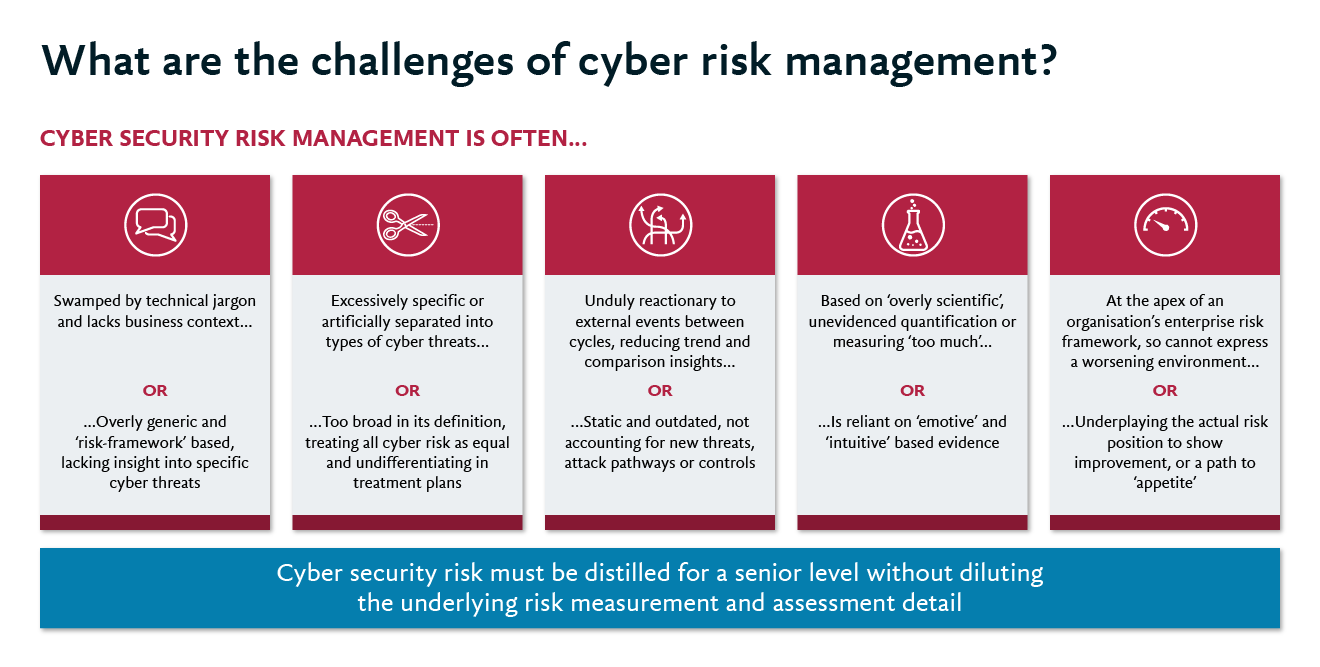
The underlying challenge is how to cut through the noise to understand how the threat environment is impacting the organisation and whether current controls are mitigating the risks to an acceptable level or not.
The way forward for your cyber security
With leadership teams finding it hard to see the real picture, there’s clearly a need for a simplified model that can distil cyber security and make it intelligible for senior management, without diluting the underlying detail of the risk assessment and measurement. How would this work? How could you apply it in your business? Six priorities stand out:
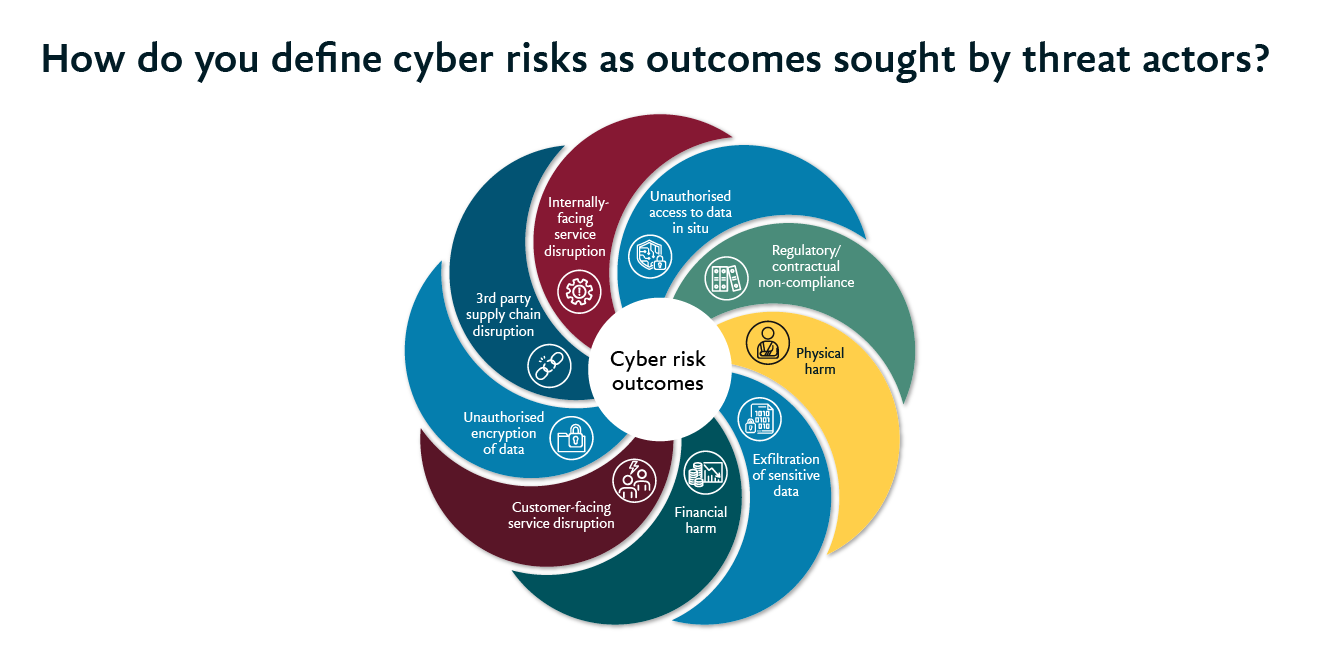
1. Clarify the outcomes in business terms
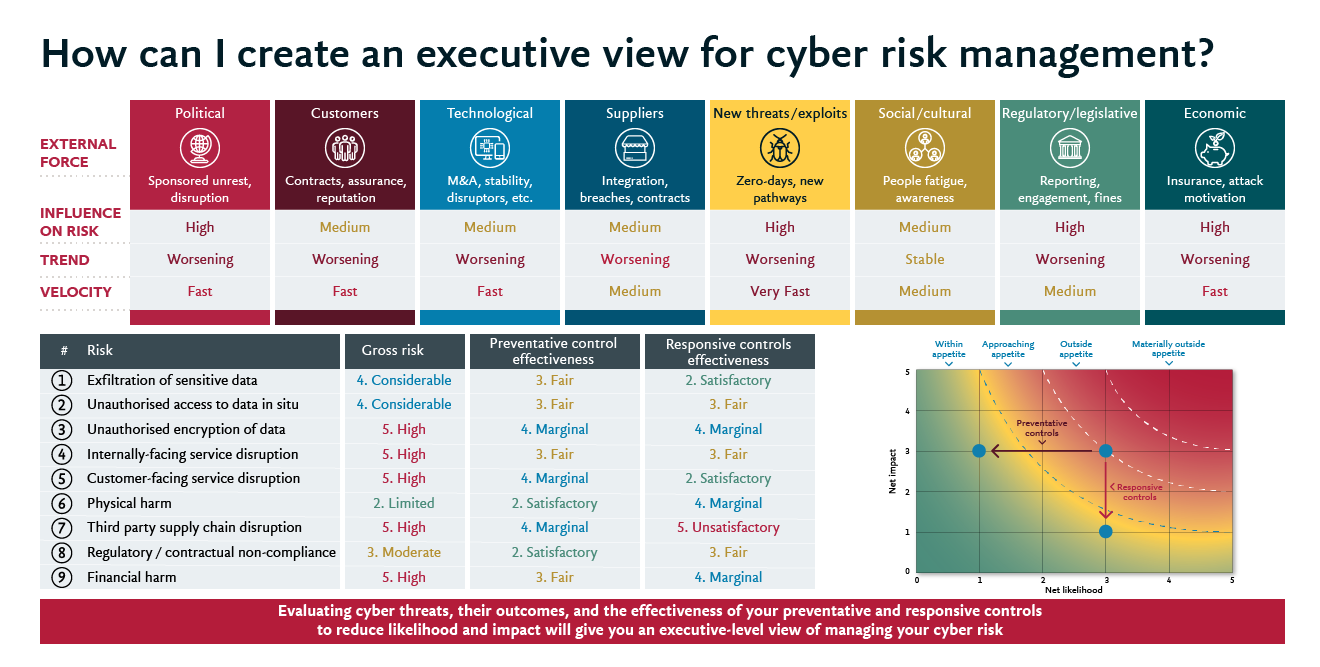
The starting point is breaking down the threat landscape and resulting cyber risks into a set of easy-to-understand business outcomes. In our view as cyber security consultants, there are nine discrete business outcomes that could result from a cyberattack (see graphic for full list). Managing a finite set of risks defined in business outcome terms should underpin everything you do in cyber security.
2. Assess the potential impact
With the threats distilled, you can then assess the likelihood and impact of each outcome by judging the external threat against your readiness to meet it. For example, a combination of encryption and strong access controls might have made it harder for hacktivists and state actors to steal sensitive data. But you may still be vulnerable to an inside breach from a disaffected member of staff due to poor internal data loss prevention controls.
3. Gauge the capabilities needed to respond
The next step is ensuring you understand the capabilities (or controls) required to mitigate these risks. Industry recognised frameworks such as the National Institute of Standards and Technology (NIST) cyber security framework or the Centre for Internet Security (CIS) Controls inventory can be useful guides to ensure you are covering all the bases. Importantly, you must have clear line of sight from your controls to your risks, and a transparent mechanism for assessing the coverage and effectiveness of your safeguards.
4.Target and tackle weaknesses
By understanding the threat landscape and cyber risks in clear business terms, you can build a realistic cyber security roadmap targeted at remediating your highest priority risks and levelling-up your cyber capabilities to build resilience. As a result, your executive team and Board will be in a stronger position to provide challenge and oversight in managing the risks and directing resources where they can have the most impact. As part of this analysis, cyber teams can also bring recommended interventions to life and frame them in language that makes sense to senior management. Some previously underestimated and under-addressed threats may need urgent intervention. But it may also be possible to scale back in other areas, releasing time and money to mitigate more pressing threats.
5. Build risk assessments into business strategy
Examples include judging the trade-off between an early launch of a tech-enabled innovation ahead of competitors or holding back until the potential risks are more effectively understood and managed.
In all cases, the assessment should be guided by a clear sense of how a security culture is created and embedded across the organisation, as everyone has a role to play in building cyber resilience, not just CISOs or the security team.
The other big advantage of having a business-oriented view of cyber risk is a more informed approach to setting risk tolerances. You can’t eliminate cyber risks altogether – your business would grind to a halt if it did. But by clearly articulating and weighing up the likelihood and impact of possible business outcomes, it’s easier to determine an acceptable level of risk and have conversations about whether to target investment in preventative controls (to reduce the likelihood of a cyber incident happening) or responsive controls (to reduce the impact of a cyber incident when it does happen).
6. Strengthen stakeholder assurance
Use the risk assessments to assure insurers and regulators that senior management are providing the right level of oversight and challenge of cyber risk management. We’ve seen clear evidence of this in our Section 166 reviews. For example, regulators could be concerned that certain risk measures might not be improving despite considerable investment. But on investigation, the problem might not be insufficient safeguards, but unintelligible reporting that doesn’t clearly demonstrate the progress being made.
Let’s talk
We’re working with businesses across all sectors to help them make sense of the cyber risks they face and strengthen security and resilience. Talk to us if you’d like to know more.